Every business owner is looking for ways to maximize the efficiency of their employees and provide productive working conditions. This is what makes the company grow and become better than the competition which results in bigger success.
Google Cloud is a flexible way to connect to your business. The ability to get access to various files can be essential so you can work from anywhere, and build teams from around the world. However, is your data ultimately safe?
In this article, we’ll talk about whether is it possible for your Google cloud to be hacked. In addition, you’ll learn how can this happen, and all the ways you can protect your data. Keep reading and find out more.
Is it possible for your Google cloud to be hacked?

As one of the options chosen by many companies, Google cloud offers a variety of features that explain its popularity. However, the question of whether your data is completely safe remains unsolved. While the main focus is security, it is possible that your google cloud to be hacked.
About seven years ago, it was exactly the google cloud that was targeted in an attack resulting in the compromise of information from many users. This was the main reason for doubting the safety of using the program.
However, even though it is possible to be the target of a hack, Google cloud remains a highly secure platform. This is why it is one of the most used clouding options and businesses are relying on it.
How can this happen?
While we’ve established that you can be a target for hackers, it is also important to know how can this happen. There are three major ways how can attackers gain access to your account which we’ll go through in the following.
Leakage of login information
The first way is quite an obvious one. If any of your login information gets somehow leaked, your whole platform is at risk if the login gets in the wrong hands. While you won’t do this intentionally, by logging on to public networks you are compromising your account.
In addition, it would not be wise to go to the access keys and oversee login information or any secrets posted on your cloud. Do this only at work or in cases you are certainly sure about the safety of the network.
Unsafe computer

Another way how can you be at risk is if you are using an unsafe computer. As soon as hackers get access to your computer, they can get everything they need using your saved logins. They can also track the keys you press and figure out login information that can be used to get onto your cloud.
Access to the computing instance
The instances are all separate engines that contribute to the functionality of the platform. With that, when you get access to them, you can easily enter the cloud and get all information needed. This is highly dependent on what you give access to the identity of your account and its permissions.
In case a hacker gets access to your to compute instances, they can get into all of the files shared on your cloud.
How to protect your Cloud platform
While there are certain ways your cloud can be targeted and hacked, there are also ways that you can protect yourself. By applicating these methods, you will surely contribute to working on a much safer cloud which will make your whole business functionality better, as www.consoleconnect.com suggests.
Improve the authentication method

Instead of letting your employees log in with only their passwords, you should consider implementing an additional authentication method.
In this case, the google cloud can be enforced and your employees will require authentication using multiple factors. That way, even if you share your password, nobody will be able to enter. Everyone will need to do further validation to acquire permission and login into their accounts.
There is a lot of information you can find on how to enable multiple authentication factors for your company. This step is quite easy, so be sure to implement it on time and increase the security on the platform.
Password policies
To increase the protection of passwords, there are special policies that can be used during the password creation period. For example, you can enable certain symbols, demand a certain amount of characters, and use numeric characters.
This is not done on the cloud, but on the domain administrator. It is also an easy method that significantly increases security, so be sure and do it.
Track activity and access
Frequent account observations are a healthy way to see how the cloud functions and try to spot potential malfunctions. With the ability to see the activity of each employee, and what access they have, you can surely prevent certain situations.
Frequently change the keys
The service accounts have no access to the console of the platform but are used for the programming interface only. They can have multiple keys which you can frequently change. That way, you are shortening the window in which an attacker can get inside, and you are increasing the protection.
VPC implementation
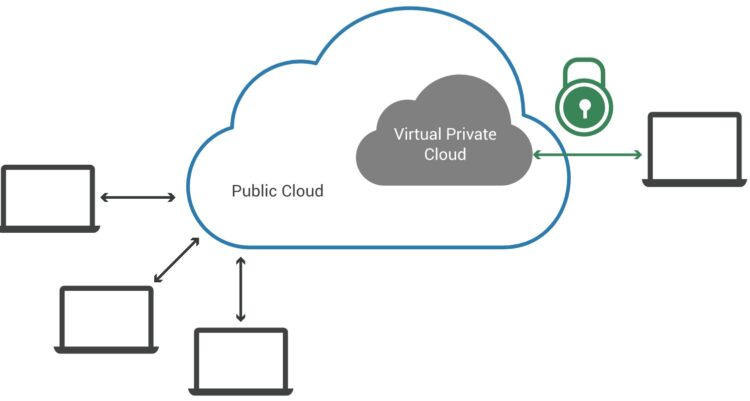
By using virtual private clouds, you are adding security measures. This means that you are creating a perimeter of service which only lets people who have been granted access to the VPC enter the cloud. Anything outside of the virtual platform will be denied to enter.
Besides added protection, the VPCs offer various functions. For example, they are making the managing process easier, and they boost the performance of the clout itself. They are fast and can be used whenever you need access to data.
With a reach across the world, you will have no obstructions and can incorporate teams from around the globe to work simultaneously. They have almost no downtime which means you can use the VPC whenever you need it and get to the files required for the work.
Lastly, it is important to know that you will be able to use your infrastructure. In addition, the visibility of the actions and ability to monitor each activity grants control you will surely appreciate.

